Cyber Security: A Worldwide Issue
By: Dorothy Riggs, CFE
Who Dabbles in Cyberspace?
October is National Cyber Security Awareness Month (NCSAM), which was designed to involve and inform the public regarding cyber safety issues. One thing Hillary Clinton and Donald Trump agreed on during the first 2016 presidential candidate debate held on September 26th, is the fact that cyber security should definitely be a top priority for the United States Government. And I’ll add, for the world at large given that so many players worldwide conduct cyberspace activity. For those of you who may have been stuck in a time warp, cyberspace is described as the realm where electronic or computer network communication occurs. The make-up of the cyber realm is vulnerable to a vast spectrum of risk, which is why this issue is so important.
Nowadays most people use some type of electronic computer product. Reportedly American adults spent eleven hours per day using electronic media devices in 2014. According to a 2015 Time.com/Money article, more than three billion people are internet users. Statistics reveal that one out of every seven married couples in the United States met online. Boy, times have certainly changed compared to when I grew up in the late 70’s and 80’s. It astonishes me how connected we are and how much we rely on electronic communication in our current society. We now use electronic devices for practically everything: banking, photos, gaming, email, texting, fitness, shopping, dating, news, reading, phone calls, calendars, writing, and the list goes on and on and on. The Statista chart below provides a breakdown of commonly used electronic devices and their daily usage by American Adults in 2014.
Because so many individuals, organizations and government agencies use devices that are active in cyberspace, a plethora of valuable data can be accessed in the cyber realm, which makes it a hotbed for fraudsters and other criminals.
Sharpen Your Awareness of Cyber Crime
Criminal activity carried out by means of computer devices or the Internet is called cyber crime. Criminals exploit cyberspace vulnerabilities to steal information and money. They can also disrupt, destroy or halt delivery of essential services. In the United States the FBI is the leading agency when it comes to investigating cyber offenses. They have a specialized division called the Internet Crime Complaint Center (IC3) which provides a convenient reporting mechanism to the public. The IC3 received 288,012 Internet crime reports in 2015, which is likely only a drop in the bucket since many victims fail to report electronic crimes due to embarrassment or other issues. To give you an idea about your vulnerability to cyber crime, in 2011 it was reported that Facebook social media accounts are attacked by hacks 600,000 times per day. In February 2016 a massive data breach was reported by the U.S. Internal Revenue Service (IRS) in which over 700,000 social security numbers and other sensitive information may have been stolen. On September 22, 2016 Yahoo confirmed that data associated with 500 million user accounts have been stolen in what is possibly the largest cyber security breach ever. Susceptibility to cyber crime is all inclusive. All cyberspace users are vulnerable; small businesses, large corporations, individuals, government agencies and so on. Here’s a list of commonly used cyber crimes or scams that individuals and organizations should be aware of:
- Ransome ware – a type of malware that encrypts or locks valuable digital files and demands a ransom to release them. Ransome ware is usually delivered by clicking on a link in an e-mail or by visiting a website that has been seeded with malicious code.
- Business E-mail Compromise – a scam targeting businesses and initiated by compromising legitimate business email accounts via social engineering or computer intrusion techniques to facilitate fraudulent transfer of funds. (Individuals have also been targeted by e-mail compromises for the purpose of conducting fraudulent transfers of funds.)
- Overpayment – Normally an individual places an item for sale via an Internet ad. The buyer sends payment exceeding the sales price and instructs the seller to send excess funds to another business or individual. This tactic has also been used in employment related scams. Individuals receive payment in excess of expected wages after accepting work-from-home positions. The individual is asked to send excess funds back to the supposed employer or to a third party.
- Advanced Fee – a business or individual pays money to someone expecting to receive something of greater value in return. Instead something of significantly less valued or nothing is received. This tactic is often used in Lottery / Sweepstakes scams. Individuals are asked to pay winning prize taxes and fees up front, but never receive winnings.
- Charity – Using deception to obtain money from businesses or individuals who believe they are donating to legitimate charities.
- Confidence /Romance Fraud – An Individual is tricked into believing that they are in a real relationship and is conned into sending money, personal or financial data, or items of value to a fraudster. Individuals have also unwittingly laundered money for fraudsters. In some cases victims end up serving time because his or her perceived bond with the fraudster aka love interest is so strong that they continue following the crooks money laundering instructions even after authorities have made them aware of the criminal offense.
- Credit / Debit Card Fraud – Theft or fraud committed using a payment card or any similar payment mechanism as a fraudulent source of funds in a transaction.
- Data Breach – Affect large corporations and individuals. Sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by someone who is unauthorized to do so.
- Extortion – The use of intimidation or undue exercise of authority to exact money or property from individuals or organizations.
- Identity Theft – Someone steals and uses personal identification data, such as Social Security number, name, date of birth, or address without authorization to commit fraud and/or other crimes.
- Lottery / Sweepstakes Scams – a person is notified that they won a lottery/sweepstakes they never entered.
- Phishing / Vishing / Smishing / Pharming – Defrauding an individual or business of personal or financial information, the information is then used to facilitate other crimes.
What Can You Do to Mitigate Chances of Being Victimized By Cyber Criminals?
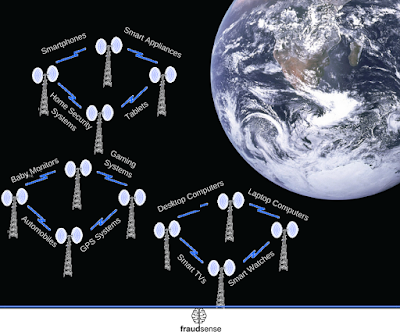
As previously mentioned, if you use a modern automobile, GPS system, smartphone, smartTV, desktop computer, tablet, laptop computer, gaming system, smartwatch, smart appliances, home security system, baby monitor and the like, there’s a substantial likelihood that you will be targeted by cyber criminals. The suggestions below are not guaranteed cyber crime blockers, but they can help reduce your chances of being victimized.
- Set strong passwords and change them periodically. Strong passwords have at least eight characters consisting of a mix of upper and lower case letters, numbers, and special characters. Don’t share passwords with anyone.
- Do not click on links, open attachments or pop-up screens from sources you are not familiar with.
- Guard personal information. Limit the amount of personal data you share online. Technically, there is no delete button on the Internet. Even if you delete content someone may have saved it or taken a screenshot. Don’t provide Social Security numbers or account data to people contacting you online. Fraudsters and other criminals can use social media profiles and other data you share online to commit offenses. Take note that banks or reputable companies don’t typically ask for personal identification data via text or e-mail.
- Use secure internet connections when possible. Be extremely cautious of information you share when connected to public Wi-Fi networks.
- When shopping online make sure the website uses secure technology and closely examine the web address on the check-out screen to make sure it begins with https. The 'S' at the end of HTTPS stands for 'Secure'. It means all communications between your browser and the website are encrypted. Also, make sure a small locked padlock symbol appears on the page.
- Make sure your virus protection software on electronic devices is active and up to date.
- Use caution when downloading apps. They may contain malware.
- If you receive a suspicious e-mail, especially if a monetary request is made, contact the company or individual directly to verify the communication using a contact number from a legitimate source. Don’t use contact numbers provided within the suspicious e-mail. After reporting confirmed fraudulent e-mail to the proper authorities, delete the e-mail from your device.
- Be cautious about negotiating checks from companies or individuals you’ve met online and have no other knowledge of them. Attempt to verify checks prior to cashing or depositing them. Be careful about sending funds via wire transfer, check or any other means to companies or individuals you’re not familiar with.
- Verify the validity of Go-Fund-Me accounts and charities before donating funds to insure the legitimacy of the cause or need.
- Disable remote connectivity when the feature is not in use. Most mobile phones and other devices are equipped with wireless technologies, like Bluetooth, which enables them to connect to other devices.
- Workplaces should provide cyber security training and establish clear policies & procedures for the organization’s networks and information for all employees. In addition to adhering to the previous tips, employees should not install or connect any personal software or hardware to workplace networks without authorization from the IT department. Any suspicious or unusual computer problems should be reported to the IT department.
- Workplaces and individuals should make back-ups or copies of all important data.
- Change the manufacturer’s default passwords on all software.
- Workplace IT departments should monitor, log, analyze and report successful and attempted network intrusions. In the United States US-CERT (United States Computer Emergency Readiness Team) provides assistance regarding cyber security.



Comments
Post a Comment